In a previous blog I explored two ways to launch a command prompt in Windows as the System user. Since I jumped on the Windows 10 bandwagon, slept on the sidewalk to be the first one in my neighborhood to have it, I wondered if the methods mentioned in that blog would work in Windows 10. Let’s find out.
Quoting from the previous blog, let’s review our methodology: The first method requires the installation of PsExec, which is a component of the PsTools download provided by Mark Russinovich PsExec v2.11. Once you have downloaded this and extracted it to a folder, you can proceed to the next step. Launch CMD as an administrator and navigate to the folder where you unzipped PsTools.zip. If you want to take a look at your options, type psexec /?. The output is shown in figure 1.
Figure 1
Type the following command:
psexec –i –s CMD (not case-sensitive)
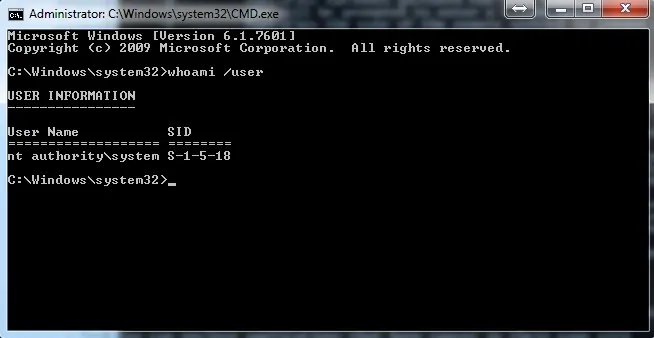
This will open a new command prompt window which doesn’t look all that impressive on the surface. However, note which user account holds sway within this window (Figure 2 below):
Figure 2
Notice that you now can type commands as if you are SYSTEM! Feel the power! For example, using the sc command, check for a service that is listed as UNSTOPPABLE and disable it (it will likely still not allow you to stop it directly, but disabling it and rebooting accomplishes the same task). My current box has no services running that are unstoppable, but figure 3 demonstrates where you to look to see it.
Figure 3
I am pleased to report that the above method continues to function correctly in my version of Windows 10 [Windows 10 Pro x64.]
How about the second method? To save you doing a bunch of work for nothing, let me reveal at the outset that I could not get this method to work correctly. But to jog your memory, I reiterate the method below and then explain my results at the end.
The second method may be to your liking as well. It involves creating a test service (to be used just for the purpose of creating the CMD window with the SYSTEM credentials) and then starting this service. Create the service with this command:
sc create cmdsvc binpath= “cmd /K start” type= own type= interact
The word after ‘create’ is what you have named your new service – feel free to give it any (unused) name you desire. In this command, the service name is cmdsvc.
Now to start the service: sc start cmdsvc
If you are running Windows 7, this will cause an icon to appear on your taskbar demanding your attention. If you click on it, this window appears:
Figure 4
Select ‘View the message’ and your desktop briefly disappears and the screen is blank except for your new command prompt window. Once again, verify your status with the whoami command and see that you are once again wielding the awesome power of the SYSTEM account.
If you leave this window up for several minutes, you will end up getting logged off. To prevent this, do what you need to do in this window and then exit to get back to your familiar desktop.
If you are running an OS higher than Windows 7 (for example, Windows 10, which is the subject of this blog), you will NOT see the above message, rather you will see an error message. To complete this same process in that situation involves a registry modification. Proceed with caution if you are not one to regularly change the registry as system damage can occur. Otherwise, take a deep breath and perform the following. Type regedit or regedt32 to get to the registry. Then navigate to this location:
HKLM\System\CurrentControlSet\Control\Windows
Once there, look for DWORD titled NoInteractiveServices, and change its value from ‘1’ to ‘0’ and then close the registry.
Now to start the service you just enabled, which is the Interactive Detection Service.
sc start ui0detect
Now you can return to the command above with which you created your sample service and start it, because now it will work.
sc start cmdsvc
Now that the Interactive Detection Service is running, the behavior will match the behavior I described above for Windows 7. Keep an eye on the task bar, because an icon will appear there after the above command. When you click it, you will see a window similar to figure 4. Clicking ‘View the Message’ appears to work, because you will see the Command Prompt window appear on the plain background, but for the life of me I was unable to type inside that window. If you get this far, and your results match mine, no keyboard or mouse input has any impact. Don’t panic, because if you just let it sit there, it will shortly log you off, and upon logging back in, you have resumed control of your computer. If you find a way to make the second method work correctly, I would love to hear about it.
I once again suggest using this in a test environment or on lab-type computers as serious damage can be done – unintentionally, of course – when you are typing with SYSTEM authority.
If you have any comments or questions, please feel free to post them….
Until next time.
Mark Jacob
Cisco and CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ



