See our class schedule for complete Course Schedule Training.
Classes are held in Phoenix, AZ and can be attended online from anywhere in the world with RemoteLive™.
Instructor: Rick Trader
Video Transcription:
As an Administrator, I commonly come across a situation where I have a resource out on a file server and a user happens to be a member of one, two, or even maybe multiple groups and all have access to that resource.
As an example, let’s say I have on a share on a file server Sales Reviews. It’s a folder where I’m placing all the reviews of all the employees in the Sales Department.
The only people that should have access to this folder should be the members of Management and you must be a member of the Sales Department. In other words, you have to be a Sales Manager.
In the past, in order to accomplish this task, we would have to create a group. We would need to add any member that was a member of Sales, and a member that was a member of Managers into that group to create an appropriate group.
This meant we would need to maintain, three different groups. A Managers Group, a Sales Group, and now this new group called Sales Managers that would also include the sales users.
In Windows Server 2012, one of the new features is the ability to enable a feature called Kerberos Armoring. This allows us to do Compound Permissions to the resources without actually having to use Dynamic Access Control.
Let’s get started.
First I need to go into my Active Registry structure and create a set of users that I’m going to use for this.
In this situation Fred, myself and Wilma are my three users in the Sales Department.
Fred and Rick are just regular Sales employees. Wilma is a member of Sales and she also happens to be a Manager.
If I come into the Sales Group, you will see Rick, Fred and Wilma.
If I come into the managers group you will only see Wilma.
So that’s the first step.
The next step will be to enable what’s called Kerberos Armoring. I’ll bring up my Group Policy Object.
I’ve already got Group Policy launched on this machine and I have a Group Policy that I created but haven’t configured it yet, called Kerberos Armoring.
I’d want to link this Group Policy Object to the OU where I’m going to have my servers that are going to have these permissions.
I’ll come in and I’ll go ahead and Edit this Group Policy Object.
The settings that we’re looking for are both Administrative Template settings.
I’m going to use the Filter On feature.
I filtered on just the word armor and this brought up for me two Group Policy line items.
One for the KDC.
This is actually going to enable claim support, which you don’t have to worry about claims in this demonstration.
I’m also not worried about Arming from the standpoint of Dynamic Access Control but I want to enable Armory to support Compound Authentication. I’ll go ahead and edit it, and I’m going to enable it.
That enables it from the Server-side and then on the Kerberos side we also have Kerberos client support for Claims Compound Authentication and Kerberos Armoring.
Again I’m going to armor that, or configure that, so it’s now enabled.
Next I want to link this to the OU where the Server resides. I’m going to link this to the sales OU.
The next step would be to restart the computer or run a GP Update on the computer that has the Group Policy assigned to it, so it’s server 3.
I’ll come into server 3 here. I’m just going to run a gpupdate /force in PowerShell.
I have a tendency to run them twice. Now you don’t have to run them twice, this is just my own personal safety net when I run a Group Policy. This way I make sure it does get it.
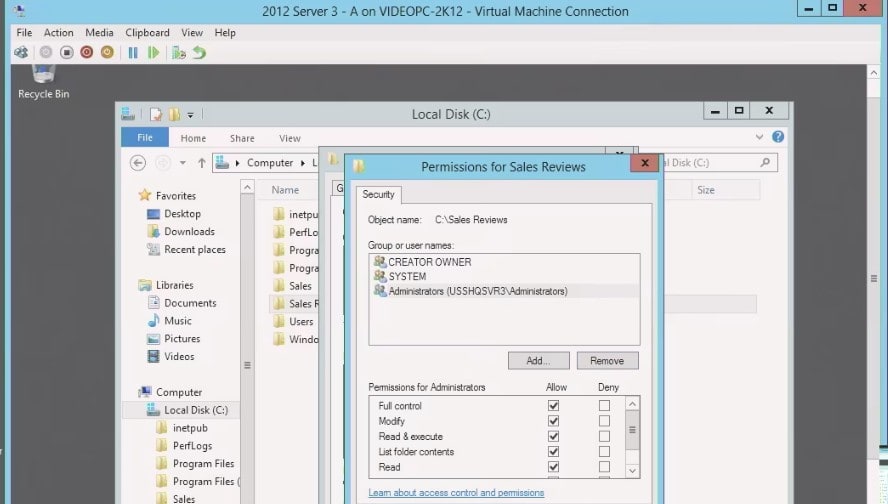
My Group Policy had been applied. I’ll come down to my folder structure, and I already have a folder on my C drive called Sales Reviews.
Here is the Rick Quarterly Review.

Of course I don’t want Rick to be able read this so I will g o into the Sales Review folder and bring up the Properties.
Look on the Security tab and look at our Default Permissions.
We’ll see that we have anyone that’s a member of the Administrative Group users group by default have read permissions.
We want to remove the users group, so I’ll select Advanced.
I’m going to go ahead and Disable Inheritance permissions.
One of the changes they made instead of calling it “Add,” is now called “Convert inherited permissions into explicit permissions on this object.” I’ll select this option.
I’ll OK then Edit, now remove the Users group.
In a lot of organizations, it’s up to the organization to whether or not you’re going to leave the Administrators in there or not. I’m going to leave the administrators in.
Now let’s go set those complex permissions.
If I click Advanced.
I’m going to come in, I’m going to do a “Add” permission.
My security principle is going to be my Authenticated Users group.
This way I ensure I catch all users are inside my Active Directory structure. I’m going to use Applies to: This folder, subfolders and files, and I’m going to do Full control.
At this point, if all I did was hit Apply, every user that’s in this domain, or from any trusted Kerberos realm, these users would have access to the folder.
Here’s this is a really cool feature. If do a “add condition”. We have a User, Group, Member of each, and now I’ll Add items.
I’m going to say a member of Sales. Check name, and then select OK.
Now if all I did was this then I’ve now given anyone that’s a member of the Sales Department or the Sales Group permissions to this resource. It doesn’t matter where they’re coming from, they have to be a member of this group called Sales. But I want to make this compound, I’m going to add a second item, Managers.
Then we’re going to hit OK, and I’m going to hit Apply.
Notice under my conditions here I now have Authenticated Users but they must be members of each Sales and Managers.
Now let’s go check the Effective Access permissions.
If I come in I want to select the user list and let’s select Rick. Remember Rick was just a member of Sales.
Rick was not a member of the Managers Group. Check name, and it’ll come down and do Effective permissions. Notice, even though Rick was a member of Sales, but not Managers and has no access.
I’ll come back over and select View effective access permissions again. This time I’ll do Fred.
Remember Fred was just a member of Sales. Then check Effective permissions and still no access.
Now, I’m going to go back to my Domain Controller and add one more user.
I’ll only make this user as a member of the Manager’s group.
Create new user, Dino, Flintstone, Dino F, you’re probably getting an idea of who one of my favorite cartoons was?
Set Dino’s password. Make Dino a member of just the group Managers.
Successfully added, go back over here to my server 3. Come back in for select a different user.
Let’s select Dino.
Select Effective permissions and notice that Dino also doesn’t have any permissions.
We’ve checked to verify that just a member of Sales doesn’t have permissions. Just the member of Managers doesn’t have permissions, but now let’s go check Wilma.
Remember Wilma was a member of both Sales and Managers. Voila! Wilma has full control of the folder.
We just set Compound Permissions without using the complexity of Dynamic Access Control and using things as claims.
Here’s one other thing that’s really cool.
If I return to permissions.
What if on this permissions in addition to them being Authenticated Users, and them being in these two groups, what if they have to be logged in from a computer that is a member of a specific group called sales computers.
Now I’ve just added one more level of permissions here. Not only does the user have to be a member of the sales and manager in groups, they also have to be connecting to this device or to the server from a computer that’s a member of the group called Sales.
This allows for more complexity, there is a lot of different complexities I can add.
That’s Compound Permissions. Hopefully it will make your job a little bit easier using groups. Until next time, as always, write safe.
Windows Server Instructor – Interface Technical Training
Phoenix, AZ















































