Now that we have covered subnetting to create just two networks and moved on to creating multiple subnets with Class B and Class A networks, let’s finalize this blog series topic with one more installment. Our goal in this blog is twofold: 1) Discuss subnetting a subnet and 2) discover how to use the folding method to solve situations seeking a desired number of hosts per subnet. Let’s look at the second of these goals first.
Hosts per subnet
Let’s say we are given a network of 192.168.1.0 /24 and told to subnet it so that there are at least 20 users per subnet. The first thing to realize is that our folding method can still be used to solve this problem. The second thing is to remember that when we are providing for a certain number of hosts, we must subtract two from the mathematical result because we can’t assign the network ID nor the directed broadcast address to a host machine.
The formula to keep in mind here looks like this: 2host bits – 2.
This can be stated in words: Take the number two and raise it to the power of the number of host bits, then subtract two from the result. This gives you the total number of valid hosts per subnet. Let’s use these two pieces of information to solve our problem.
Once again, if I must provide for twenty users, I can count folds on my fingers. I get two, then four, then eight, then sixteen, and finally thirty-two. It took five folds to get to a number bigger than our requirement of twenty users. The twist is to remember that we are reserving this number of bits to use as host bits. Previously we had been immediately borrowing the number of folds, or bits, as soon as we knew how many there were. Flip that around now and reserve that number of host bits. Since our problem started with a /24 mask, that means we have eight host bits available for use. We need to preserve five of them as host bits, but we still need to subnet this network. The actual number of networks is not important, just that we ensure that there are at least twenty hosts in each of the newly created subnets. If we break down that last octet in binary, now that we know how many bits to retain, we get this:
1 1 1 0 0 0 0 0
Thus we see the five host bits that we reserved, which means the other three bits are converted to ones, or network bits. In decimal, this is 255.255.255.224. If we apply the formula above, we can answer the question of how many hosts there are per subnet. With five host bits, we get this: 25 – 2 = 32 – 2 = 30. So there are thirty hosts per subnet in our new scheme. Once we have made it this far, the rest of the problem is the same as before; that is, list the network IDs, valid host IP address ranges, and directed broadcast addresses.
Viewing these results all at once, we get this:
This same strategy can be employed whether we are starting with a Class B or Class A network as well. Just make sure to preserve the required number of host bits to meet the requirements, and then create a subnet mask in binary that HAS that number of host bits. Then the rest of the available host bits are changed to network bits and then solve as usual.
Subnetting a Subnet
A typical problem of this nature usually begins with how much of a network is available from which further subnets can be created. I like to visualize this by once again referring to a piece of cake. If you go to a wedding reception and are given a piece of the wedding cake, you realize immediately that you do not possess the entire cake. If you ask for four plates and a larger piece, then you can go back to your family, cut a piece for your spouse, and smaller pieces for your kids. This is like subnetting a subnet. Once you get back to your table, you can cut your piece however you desire. There is no need to cut it evenly, especially if you want to make sure your piece is larger than your spouse’s piece.
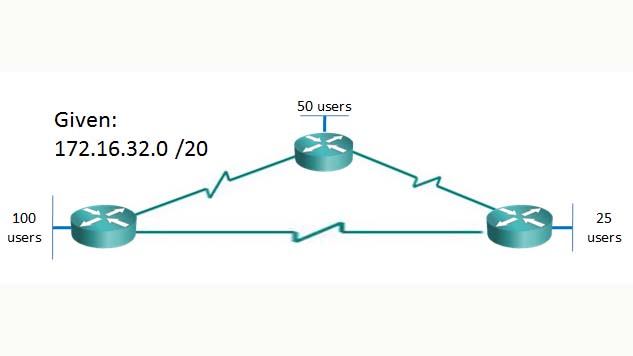
Let’s see how this looks with network numbers since we don’t actually have any cake. (The author is currently lamenting the lack of cake at his disposal.) Let’s say your organization has been assigned the 172.16.32.0 /20 network block with the following scenario:
The objective is to meet the IP addressing needs of this scenario while being as efficient as possible with our available address space.
Let’s attack this problem the way we have been solving the previous problems; that is, fold our piece of the network to match the number of required numbers. The first step is to determine the number of networks for which we are solving. At first glance, we may think that there are only three networks, the 100 users network, the 50 users network, and the 25 users network. But this leaves out the point-to-point connections between our routers. These are networks as well and must be considered in the solution. This means we are solving for a total of six networks. If we look at the given information, we immediately see that we have a Class B network with a non-default subnet mask. This means that somebody has touched our cake already, which means we don’t have the whole Class B network, we just have OUR piece of it. How big is our piece then? Looking at the slash notation, we see that it is a /20. Since we are dealing with a Class B network, that means that the first sixteen bits already belonged to the network before it was touched. This tell us that whoever touched it borrowed four host bits and made them network bits, resulting in the /20 mask. Let’s use the chart that we created in previous blog posts to see what that /20 mask means. For a refresher, here is the chart:
Since there were four bits borrowed that were added to the original sixteen network bits, we realize the borrowed bits carry into the third octet. Let’s focus on that third octet by putting our borrowed bits and host bits in their respective positions for just that octet:
Thus we see the subnet mask in decimal is 240 in that third octet, or 255.255.240.0 for the entire mask. A mask value of 240 gives us an increment of 16, which means the next subnet after ours (the next piece of the wedding cake to the person behind us in the wedding cake line, if we are still using our mental picture) is 172.16.48.0, which we determine by adding sixteen to our third octet value of thirty-two.
This answers the question of how big is our piece of the cake. Now to cut it up to satisfy our number of networks. We have counted six networks in our scenario. How many times do we have to fold our piece of the network to create six subnets? Counting on our fingers gives us three folds to get eight networks. (Two, four, eight.) If we started with twenty network bits as stated in the problem and we borrow three more host bits, what does that do to our mask? It changes from a /20 to a /23. In decimal it is 255.255.254.0. A mask value of 254 gives us what increment value? No matter which way you use to get your increment, the answer is two. If we list a few of these networks, we should be able to see if we have solved this problem efficiently.
172.16.32.0 /23
172.16.34.0 /23
172.16.36.0 /23
.
.
.
Take a look at the first network and ask yourself, “How many hosts are in that network?” A mask of /23 means there are nine host bits left. Using our strategy from the first part of this blog tells us we can double until we have counted nine fingers, two, four, eight, …until we get to 512. Then we have to remember to subtract two from the result. This means there are 510 hosts per network in our new scheme. What is the biggest network in the scenario? I see one network with 100 users. So we are wasting 410 addresses (510 – 100) in our biggest network and even more in the networks with fewer users. What about our point-to-point connections? There will never be more than two hosts on these networks, which means 508 IP addresses will be wasted for each of these in our scenario. It seems we have failed to meet the objective of efficient use of address space. How can we fix this?
The answer is called Variable Length Subnet Mask. This is a topic you are expected to know in order to pass the ICND-2 test, or the Composite Exam. So it pays to address it here. The key is to solve for you biggest network first and work your way through the problem. Let’s try it. The network with the greatest number of clients is the one with 100 users. How many host bits do we need to achieve 100 users? Double, double, double until we get to 128. It takes seven fingers to get there. This means we need to retain seven host bits for that 100 user network. The mask in binary looks like this: 11111111.11111111.11111111.10000000. In decimal this is 255.255.255.128. Which octet is interesting? The quick way is to look at the octet whose subnet mask value is neither 255 nor 0.A The foolproof way is to see in which octet the string of ones ends. Either way, the interesting octet is the fourth one. The increment with a 128 mask is also 128. So let’s list our first piece of this solution.
172.16.32.0
172.16.32.128
If the next network starts at 172.16.32.128, then the first one ends with a broadcast address of 172.16.32.127 and there are 126 possible host IP addresses, which achieves the desired 100 user network. What is the next biggest network? It seems the one with 50 users is our next target. Following the same strategy tells us we need six host bits to have 50 users per subnet, because it took six fingers, or six doublings, to get a number bigger than 50. So the mask for THIS subnet moves from the previous mask, and is now 11111111.11111111.11111111.11000000, or 255.255.255.192. This gives us an increment of 64, and the interesting octet is still the fourth one. Continuing where we left off from above, we get this:
172.16.32.0
172.16.32.128 Since we have an increment of 64, we add that to our current position of 128, with a result of 172.16.32.192. Putting this all together, we get this:
172.16.32.0
172.16.32.128
172.16.32.192
Now the next network down in size is the one with twenty-five users. Let follow our procedure again. The number of fingers to get a number larger than twenty-five is five. So the mask is 11111111.11111111.11111111.11100000, which is 255.255.255.224. A mask of 224 gives us an increment of 32 and it is still the fourth octet which is interesting. Let’s list them:
We now have networks which meet the needs of 100 users, 50 users, and 25 users respectively.
All that remains is to solve for the point-to-point links. Good design strategy (although this is not absolutely required) is to put the point-to-point networks at the top end of the network range. As we saw in the beginning of this problem, our piece of this network went from 172.16.32.0 all the way to just under 172.16.48.0. Let’s use that information to our advantage and work backward from there to establish our point-to-point networks. Since we have already determined that the maximum number of hosts in our three router to router networks is two, let’s count fingers to see how many host bits we need (keeping in mind that we must subtract two from the result). Two, four, done! Mathematically it looks like this: 22 – 2=2.
(Side note: Cisco allows a /31 mask on point-to-point links, but this is not on the CCNA level cert exams. I mention it because you may see it in your organization.
This means the mask for the point-to-point links is 11111111.11111111.11111111.11111100, or 255.255.255.252. A mask of 252 gives us an increment of four, and it is the fourth octet that is interesting. Since the next network starts at 172.16.48.0, we must come back four from there. That puts us at 172.16.47.252 /30. This solves one of the point-to-point links. Let’s do the same for the other two. Coming back four more from 252 gives us 248. Coming back four from that gives us 244. Let’s see how that looks when we list our P2P network information:
The valid host IP addresses are the actual addresses that will be placed on the router interfaces.
If you imagine your entire available network address space as a whole pie, then it helps to see how these individual slices we have made might look. Although figure 1.1 is not exactly to scale, it does help us see what happens as we move our subnet mask bits to match the needs of the network design.
If you decide to continue creating your point-to-point links from where you left off instead of putting them at the top end of your network, you would just start with the .224 and do three networks with an increment of four. It would look like this:
Once you master this folding technique, you will approach certification exams, and real world subnetting, with a completely different attitude. I often say that once this all makes sense, you will hope for an exam where every question is a subnetting question. In the meantime, all it takes is practice, practice, practice. I have a couple of recommendations for websites that will allow you to do subnetting problem after subnetting problem. A good goal is to be able to solve any of the problems on these websites in a minute and a half or less. Try these:
San Bernardino Valley College: IP Subnet Practice Page
Happy subnetting!!
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
For previous Subnetting posts see:
Subnetting – Folding the Paper
Advanced ‘folding the paper’ subnetting concepts
A How do you determine the interesting octet if you have a Class B network and you borrow eight bits, or a Class A network where you borrow eight bits or sixteen bits? In this case you end up with a mask where all octets are either 255 or 0 value. In this event, the interesting octet is the one where the string of ones ends, which is also the octet before the 0 value.







